FAQ
What are the changes of the new ISO/IEC 27001:2022 volume?
In October 2022, the widely recognized international standard for information security, ISO 27001:2013, underwent an update and the new version, ISO/IEC 27001:2022, was published.
Over the past nine years, ISO 27001 has gained significant acceptance in various industries. Although the latest revision introduces only a few changes, it is crucial to closely examine and understand these modifications. In this discussion, we will explore all the changes in ISO 27001:2022 and compare them to the previous 2013 version.
Summary of Changes in ISO 27001:2022:
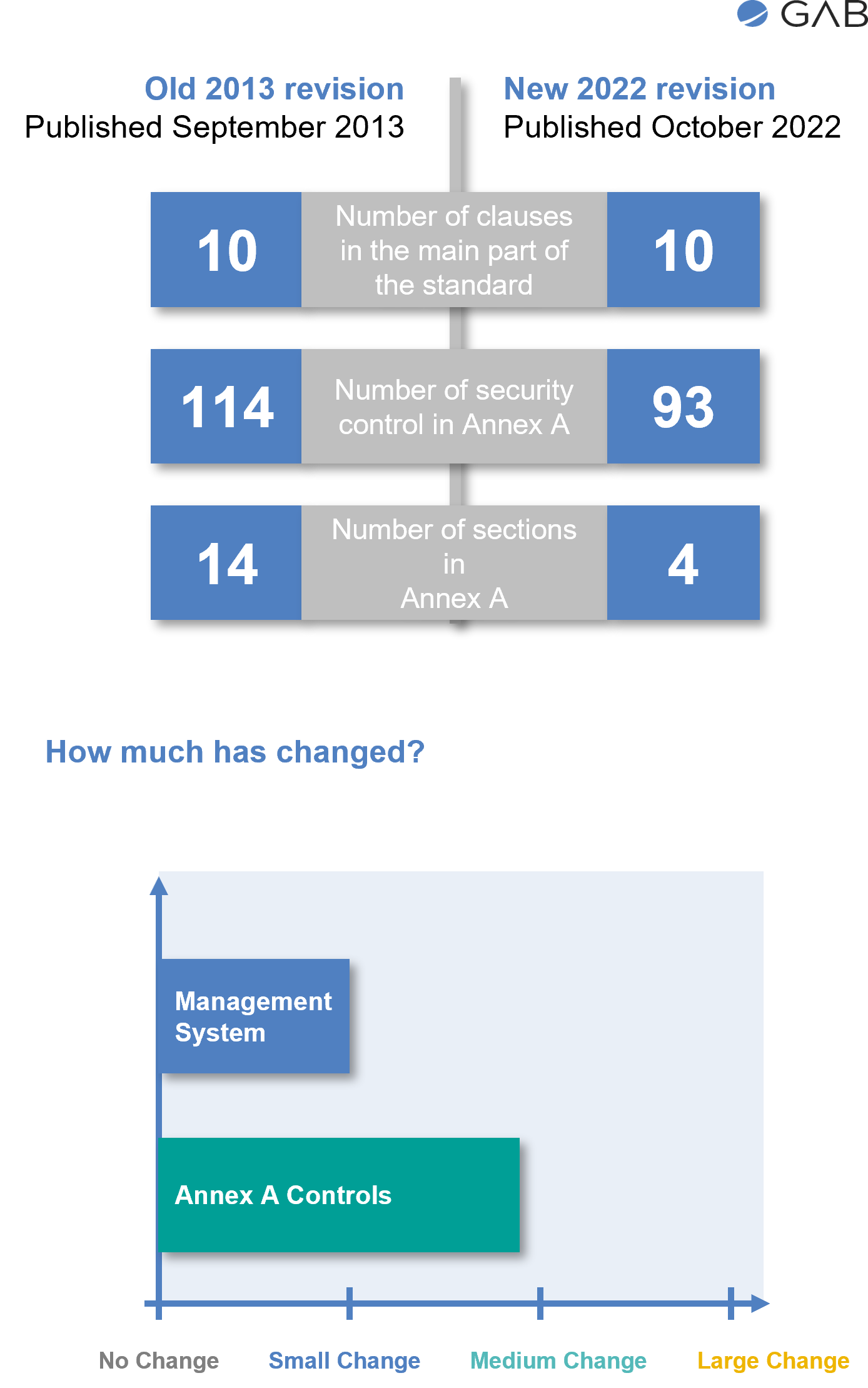
1. No major changes to ISO 27001:2013 Mandatory Clauses 4 to 10: The essential requirements outlined in the mandatory clauses of ISO 27001:2013 remain largely unchanged in the 2022 version.
2. Controls now grouped into 4 main domains: In ISO 27002:2022, which provides guidance on implementing the controls of ISO 27001, the controls have been restructured. Instead of the previous 14 categories, the controls are now grouped into 4 main domains: Organizational, People, Physical, and Technological.
3. Hashtags for easier reference and navigation: To enhance usability and ease of reference, ISO 27002:2022 introduces the use of hashtags. These hashtags can aid in navigating and locating specific controls within the document.
4. Decrease in the number of controls: The number of security controls in Annex A has been reduced from 114 in the 2013 version to 93 in the 2022 edition. This decrease is a result of merging certain controls while no controls were completely eliminated.
5. Introduction of new Organizational and Physical controls: ISO 27002:2022 includes new controls in the domains of Organizational and Physical security. These additions aim to address emerging security challenges and align with the evolving landscape of information security.
Overall, the changes in ISO/IEC 27001:2022 primarily focus on the restructuring and consolidation of controls, making the standard more concise and user-friendly while adapting to the changing security landscape.
Changes in the Structure of Management System Requirements:
There aren't many significant changes there, but a few that deserve comments:
1. 4.4 Information security management system: This new clause emphasizes the identification of processes and their interactions within the information security management system. This requirement aligns with ISO 9001 and allows for the design of process interactions using diagrams and flowcharts.
Annex A, the controls listed in Annex A are not meant to provide a full and complete list. The standard includes clauses and notes to emphasize that while these controls serve as a baseline, organizations must conduct their own assessments to determine additional controls and risks that may be necessary based on their specific environments. Therefore, it is important for organizations to consider their unique circumstances and identify any supplementary controls and risks that may be applicable.
2. 6.2 Information Security objectives: ISO 27001:2022 requires that information security objectives be documented and made available to all stakeholders. This ensures that objectives are clearly defined and communicated throughout the organization.
3. 6.3 Planning of changes: The revised standard now mandates documented planning for all changes. This emphasizes the importance of proper planning and documentation when implementing changes within the information security management system.
4. 8.1 Operational planning and control: Organizations are now required to define criteria for operational processes. The term "criteria" encompasses various aspects, ranging from security requirements to business needs or customer requests. This allows organizations to consider a broader range of factors when planning and controlling their operational processes.
5. 9 Performance evaluation: ISO 27001:2022 highlights the importance of using evaluation methods that yield comparable results, enabling organizations to assess trends over time. This emphasis on consistent evaluation helps organizations monitor the effectiveness of their controls and make informed decisions based on performance data.
6. 9.2 Internal audits: Internal audits must now cover all organizational requirements, not limited to ISO 27001 alone. This broader approach aims to create a more comprehensive management system evaluation, ensuring that all relevant requirements are considered during internal assessments.
Annex A
Annex A, which contains the security controls in ISO 27001, has undergone significant changes in the updated version, ISO 27001:2022. The restructuring and revision of Annex A have resulted in a decrease in the number of controls from 114 to 93. Additionally, the controls have been grouped into four sections, replacing the previous 14 categories.
The intention behind this restructuring is to simplify and streamline the implementation of the standard. Overlaps and repetitions have been eliminated, and the controls have been organized into five major security attributes, making them easier to categorize.
The new Sections and Controls in ISO 27002:2022 are as follows:
- Section 5: Organizational (37 controls)
- Section 6: People (8 controls)
- Section 7: Physical (14 controls)
- Section 8: Technology (34 controls)
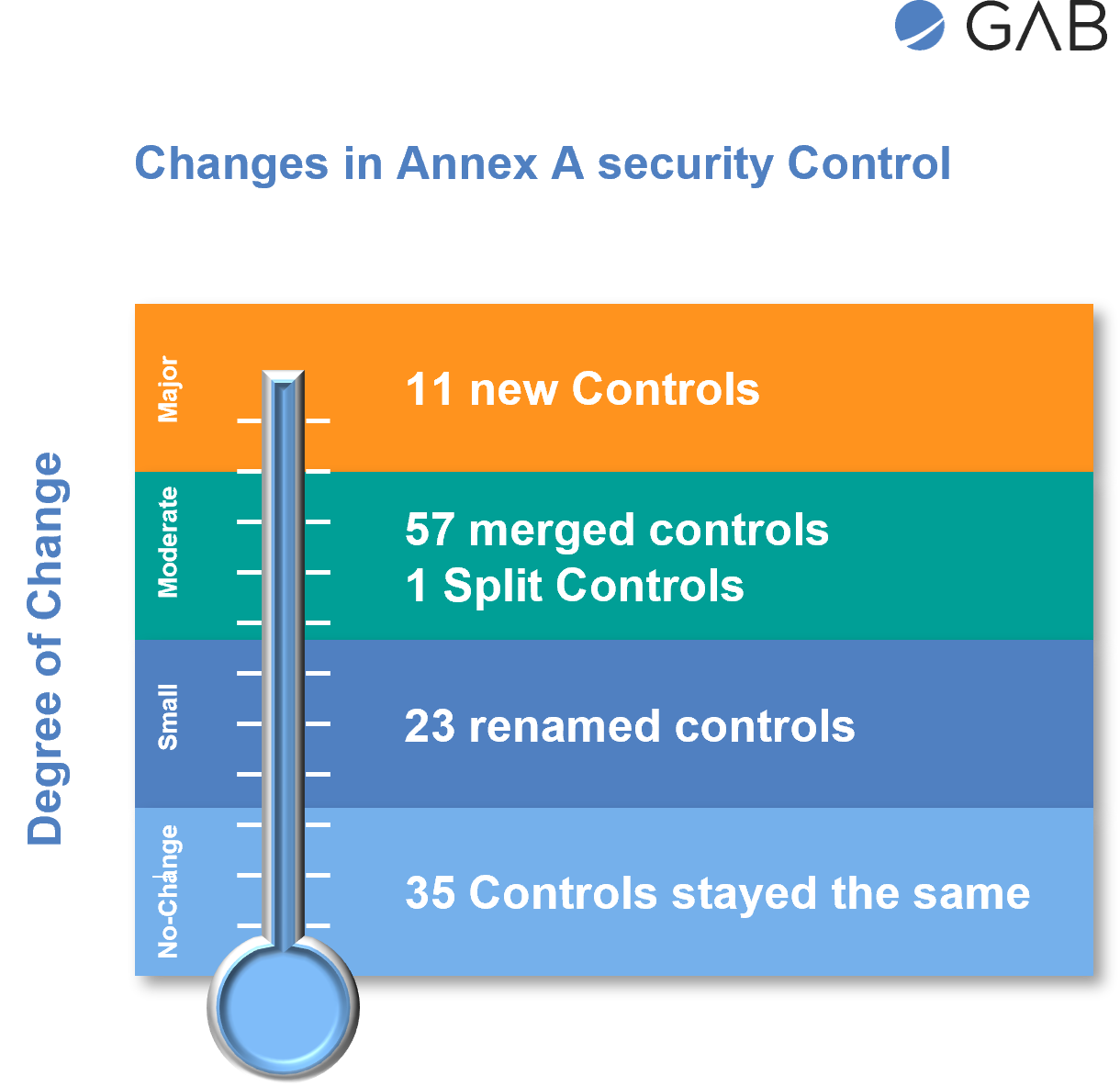
In summary, the changes in Annex A of ISO 27002:2022 can be categorized as follows:
35 controls remained unchanged,
23 controls were renamed,
57 controls were merged to form 24 controls, and
11 new controls were introduced.
These revisions aim to enhance the clarity, efficiency, and effectiveness of the security controls outlined in the standard.

The updated version of ISO 27002:2022 introduces 11 new controls that have been added to Annex A:
- A.8.28 Secure Coding: This control requires the establishment of secure coding techniques throughout the internal software development process. The aim is to reduce security vulnerabilities by incorporating secure coding practices from design to deployment stages.
- A.5.7 Threat intelligence: This control focuses on collecting and analyzing information about threats in order to effectively mitigate them. It involves gathering internal and external data related to specific attacks, attacker methods, and various types of threats.
- A.5.23 Information Security for Use of Cloud Services: This control emphasizes the need to establish security requirements for cloud services to protect sensitive information. It includes policies for the procurement, utilization, management, and termination of cloud services.
- A.5.30 ICT Readiness for Business Continuity: This control ensures that people, processes, and systems are prepared to handle disruptions effectively. The goal is to ensure that critical information and assets remain available when needed.
- A.7.4 Physical Security Monitoring: This control requires the monitoring of sensitive areas to restrict access only to authorized personnel. It includes monitoring offices, production facilities, warehouses, and other important physical premises.
- A.8.9 Configuration Management: This control focuses on managing device configurations for security purposes across all technologies and systems. It aims to ensure consistency in security levels and control unauthorized changes.
- A.8.10 Information Deletion: This control addresses the proper deletion of data that is no longer needed or exceeds documented retention periods. The goal is to prevent the potential leakage of sensitive data and comply with privacy and other relevant requirements.
- A.8.11 Data Masking: This control requires the use of data masking, combined with appropriate access controls, to reduce the risk of exposing sensitive information. It particularly emphasizes the protection of personal data in compliance with privacy regulations.
- A.8.12 Data Leakage Prevention: This control focuses on implementing measures, such as Data Leakage Prevention (DLP), to prevent unauthorized disclosure of sensitive information. It also includes incident detection measures for timely response.
- A.8.16 Monitoring Activities: This control emphasizes the management and monitoring of systems to identify unusual activity and trigger appropriate incident responses.
- A.8.23 Web Filtering: This control emphasizes the need to implement security measures for all websites accessed by users to protect IT systems from potential threats.
These new controls reflect emerging security concerns and align with evolving technologies and practices, ensuring organizations address current and future information security risks.